Every 39 seconds a cyber attack hits companies and government offices in the United States. Last week, after moderating a discussion with Chuck Brooks of General Dynamics on the vulnerabilities of ransomware, a non-profit that I support became the latest victim. This all too close event, that threatened millions of personal identities (including mine), is a painful reminder of a shortcoming of our connected future.
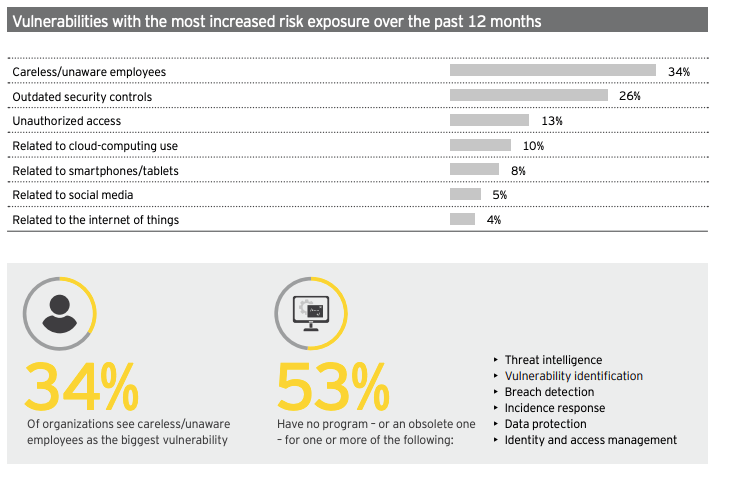
EY in its 2018-19 Global Information Security Survey assessed that last year over 6.4 billion fake emails were sent every day that led to the exposure of over 2 billion private identities and $3.5 billion of damage control. However, the majority of large corporations still do not “make ‘protecting’ part of their strategy” and almost half polled said less than 2% of their technology staff work on cybersecurity. Instead, the budget spending is primarily defensive – filling up security holes that have been previously penetrated. As more than a third of vulnerabilities are due to employee behavior, pro-activity starts with implementing good policy or cyber hygiene. As EY uncovered more than 1,200 government employees use Password123 as their login credentials, this disinfection process could not come soon enough.
Reflecting on my conversation about hacking the industrial internet with Chuck Brooks at RobotLab I am awed by his experience in the industry that includes advising two presidential administrations and the establishment of the technology group within the Department of Homeland Security (DHS). “My passion for cybersecurity issues was first established over a decade ago during the time I spent at the Department of Homeland Security’s Science and Technology Directorate. Back then, the focus was more on physical threats and Cybersecurity was just in its infancy.” Cautioning the tech-savvy group, “Since then the field of cybersecurity has evolved exponentially along with the technologies, networks, and connectivity that make up the cyber ecosystem. And the ecosystem for the Fourth Industrial Era is quite diverse and expansive, comprising software, hardware, monitoring, forensics, governance and more.”
Almost concurrent with the event, the Wall Street Journal released a report on cybersecurity profiling the threats to Industry 4.0. The most startling article was on hacking SmartCity infrastructure with the growing connectivity of parking meters, traffic lights, buildings, vehicles, pedestrian data and more. Parallel to the vision of a wired future is the number of ransomware attacks crippling hospitals, mass transit networks, emergency call centers and almost every government agency. In each incident profiled by the newspaper, the result ended in paying the attacker hundreds of thousands (and sometimes millions) of dollars in bitcoin. As an example of the current reality hitting urban administrators, last August the city of Baltimore ended up handing over $6 million to cyber crooks to turn back on their computer systems (this is on top of a reported $18 million in recovery efforts and lost revenues). The Maryland metropolis was first held up in May with a demand of $100,000. Rather than forking over the amount then, the local authorities were confident in their skills of curbing the attack. In the end that arrogance led to a tally of $10,000 a day past the deadline. In the words of Daniel Tobok, CEO of Cytelligence that has come to the rescue of 500 municipalities, paying the ransom is the new normal. “You don’t have a choice, you have to make a business decision,’ exclaims Tobok.
Brooks decries the current fatalism, he thinks that the solution lies in a better understanding of the problem and managing the risks at the personnel level. “The underlying problem is that the Internet was not built for security at its inception; it was built for connectivity and sharing communications. According to Gartner, there will be nearly 26 billion networked devices on the Internet of Things (IoT) by 2020. Moreover, it will keep expanding as the cost of sensors decreases and processing power and bandwidth continue to increase. The fact is that most of these IT networks will have some sort of an IoT-based security breach. We could be headed for a digital train wreck if IoT security standards are not adopted,” declared the security guru. He advocates for standards that cut across the traditional divisions of public and private organizations, rather he suggests forging industry consortiums, “Risk management standards will have to be developed industry by industry,” states Brooks.
When turning the mic over to the audience many participants were eager to hear Brooks’ view on artificial intelligence (AI) and protecting populations from nefarious actors. The former Homeland Security subject matter expert confessed, “I worry about protecting our critical infrastructure from nation-state attacks, especially the Grid.” However, Brooks is hopeful that new AI and ML (machine learning) technologies could alleviate the peril of America’s aging infrastructure. “AI and ML can be valuable tools to help us navigate the cybersecurity landscape. They can automate and replace a large part of the human element. Specifically, it can be used to help protect against increasingly sophisticated and malicious malware, ransomware, and social engineering attacks. AI’s capabilities in contextual reasoning can be used for synthesizing data and predicting threats.” Brooks also recognizes that “It is a two-way street. Hackers as well as defenders will employ those capabilities and are already doing so.” To counter this trend he looks to “better encryption, biometrics, analytics, and automated network security to protect networks and endpoints.” In his view, “It is a perpetual game of cat and mouse between hackers and protectors, and there is really no such thing as being invulnerable. There is certainly no such thing as privacy anymore.”
He stressed further in the Q&A the need for partnerships, “Public-private partnerships are critical to the 4th Industrial Era as there is still much to be discovered, tested, prototyped and employed in protecting us from future threats.” He provided an active example of this relationship with the Department of Homeland Security’s new agency Critical Infrastructure Security Agency (CISA). “The new entity puts a keen focus on DHS’s integral role in cyber preparedness, response, and resilience for critical infrastructure. DHS has identified 16 infrastructures deemed critical because their physical and digital assets, systems, and networks are considered vital to national economic security, safety, and national public health,” Brooks optimistically described. The profile of CISA has risen in recent months with the news of suspecting Chinese cell phone provider Huawei of using its network to spy on its users globally. As Tim Stevens of Kings College in the United Kingdom elaborates, “The concern from the West is that Huawei may have built-in certain vulnerabilities into products that they’re selling in the West that can later be exploited by Chinese military and intelligence.” Stevens cautions the rush to judgment, as the jury is still out on Huawei.
As more and more organizations cut the physical wires of enterprise servers and connect their devices, machines, and infrastructure to the cloud, technology managers are rethinking how they back up their data. In referencing the surge of ransomware attacks, Joe Merces, Chief Product Officer of Cloud Daddy, writes in Forbes, “Labeling a backup product as data protection may have worked years ago, but in today’s cyberattack-riddled world, this description no longer works or fits for the majority of backup products that continue to go by data protection.” Cloud Daddy boasts on its website as being the “Only AWS [Amazon Web Services] cloud data protection solution designed and engineered with security in mind to protect your data that is in turn meant to protect your enterprise in case of disaster.” As Amazon represents almost half of the cloud hosting market, Merces’ company represents a new class of startups that are proactively providing threat-protection behind the scenes, which Chuck Brooks and his DHS colleagues applaud.