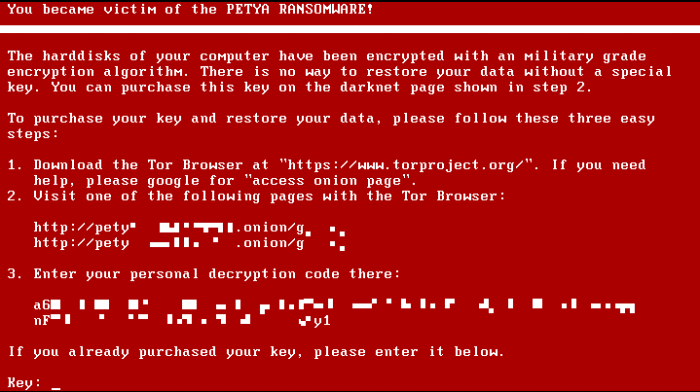
Recently, banks across the Ukraine were hit with the “Petya Ransomeware” computer virus. The malware quickly spread to Russia, Spain, and the United States forcing many to pay the criminal’s demand. This comes just weeks after the WannaCry cyber attack spread across 74 nations, completely freezing the British healthcare system for hours. As we approach an autonomous future where machines will roam our streets, workplaces, factories and homes, many are questioning how safe the world will be from nefarious actors.
Local New York cyber security expert, Chris Camacho said, “There is going to be a lot more of these attacks. We’ll see copycats, and not just for ransomware, but other attacks.” These “other attacks” will take more creative forms by infiltrating our machines.
In 2010, the Stuxnet worm infiltrated the Iranian nuclear program – targeting its Programmable Logic Controllers (PLCs) to cause their centrifuges to spin out of control. According to the famed Kaspersky Labs, Russian cyber research firm Stuxnet was originally developed in 2005 by the United States and Israel intelligence organizations to reverse the Iranian program. While it has been seven years since Stuxnet, industrial robots worldwide are still vulnerable against malicious hacks. A security report published last month by the Politecnico di Milano and Trend Micro found that:”Robots could be easily reprogrammed to violate their safety parameters.” This means that not only human workers are at risk of Baxter-like robots turning against them, but potentially billions of dollars of financial losses could affect global economies.
Tim McKnight, Chief Information Security Officer of GE, said it best, ‘enterprise cyber security is about keeping documents safe, while industrial cyber security is about making sure things don’t blow up.’ GE, the leading US supplier of Jet Engines, coined the phrase the Industrial Internet of Things (IIoT). Connecting avionics to the cloud has been a goal of the conglomerate for almost a decade, however the hinderance has been keeping the connection secure from terrorists.
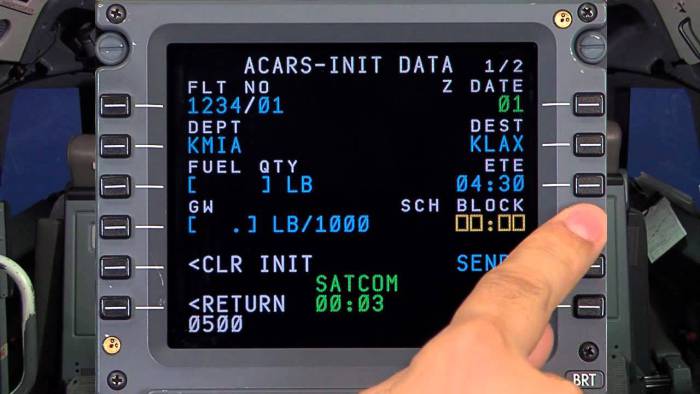
Last month the Wall Street Journal reported that the air-traffic control messaging system, ACARS, is in desperate need of an upgrade to protect against hackers. ACARS was originally built in the 1980s as a way for ground controllers to communicate with the cockpit in air. While ACARS does not connect to any mission-critical avionic systems, the fear is a terrorist could send harming information that could lead to a major catastrophe. Government regulators and industry officials have warned of the lack of safeguards, leaving millions of passengers and crew at risk everyday. Militaries have protected their air fleets from cyber attacks for decades with hardware and software modules that cost hundreds of thousands of dollars per craft. These NSA-level security platforms are cost prohibitive for airlines, and certainly for consumer autonomous vehicles that currently ship with five times more lines of code that a typical commercial jetliner.
Moshe Shlisel and Dionis Teshler, formerly with the Israel Air Force (IAF), are the founders of GuardKnoxa “comprehensive cyber security hardware solutions” company for the autonomous car market. In the words of Teshler, “What would you like protecting your safety, something that somebody invented for your PC or something from a fighter jet?” The answer to his question is their patent-pending hardware box that connects to the car’s Engine Control Units (ECUs). GuardKnox is one of the few offerings on the market that meet the stringent security and safety standards of ISO 15408 and 26262. Its core product is a “Secure Network Orchestrator” (shown above). The SNO promises to be “an easy to integrate (drop-in) cyber security hardware solution” specifically designed for Infotainment, Telematics and other external communication systems (to block against the type of vulnerabilities illustrated in the Jeep Cherokee and Tesla hacks).
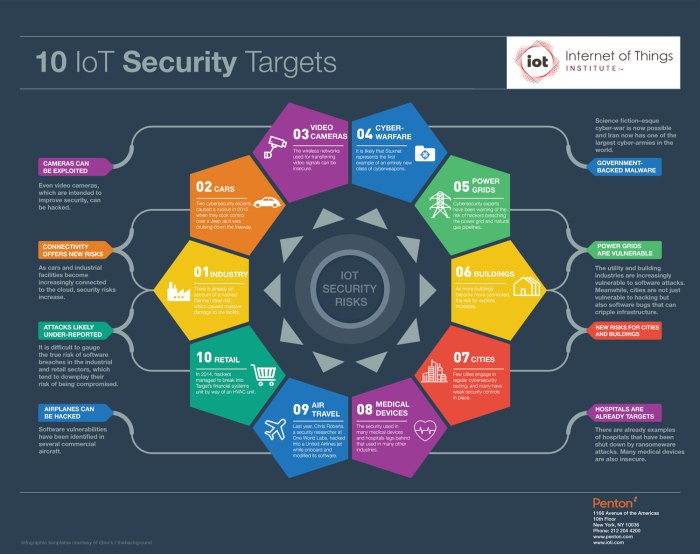
Cyber warfare targeting infrastructure is an immediate threat. As reported by cybersecurity experts Joe Saunders, CEO, of RunSafe Security. “Whether it is stealing passwords, exfiltrating sensitive data, disrupting traffic signals, taking control of a vehicle’s operations, or locking devices for ransom, IoT devices are extremely vulnerable to cyberattacks,” explains Saunders. “The underlying issue is that the operating system running on these devices often has security vulnerabilities. Additionally, poorly written software code allows hackers to take control of a device and use its own code to do malicious actions.”
Saunders points to numerous examples of attacks commandeering networked control systems. In 2013, Iranian hackers (possibly in retaliation for Stuxnet) shutdown a New York State water dam, and on Christmas 2015 hackers brought down the Ukrainian power grid. “Imagine sensors on instrumentation systems or oil rigs being manipulated, or consider the hack of a New York state water dam a couple years ago, or the shutdown of the power grid in Ukraine. We used cranks or levers to manually adjust control systems in the past. These systems are now centrally managed via software systems talking to remote devices,” says Saunders.
Saunders and his team at RunSafe are all former intelligence contractors that deeply understand the threats facing connected machines worldwide. Their proprietary Runtime App Self Protection (RASP) software inputs security directly in the “app or app runtime environments, capable of controlling app execution, detecting and preventing real-time attacks.” Saunders has already received the endorsement of Gartner, which calls RASP a “must-have, emerging security technology.” According to the company’s white paper, its patented RASP technology “addresses the limitations of external infrastructure and perimeter protection tools,” through the randomization of code, data and memory. RASP promises to “cyberharden” vulnerable systems and devices by disrupting “the traditional economics of cyberattacks and deny the routine tactics and techniques that attackers prefer.” In a sense, a hacker would have to rebuild the code on every connected device within the network to success penetrate RASP’s defense. RunSafe’s is currently marketing its solution to national defense establishments, industrial IoT, critical infrastructure and the automotive industry.
For almost a decade the US Department of Homeland Security Science and Technology Directorate and DARPA have been working with Columbia University spin out, Red Balloon Security. Columbia Professor and Red Balloon Chief Scientist, Dr. Ang Cui, explains, “Our technology is the culmination of almost a decade of work, It was designed to install easily on any device without modifying the hardware or source code and works on any CPU and all operating systems.” Cui’s technology is an “intrusion defense that provides persistent implant detection, in-device memory monitoring and situational awareness ” against any malicious activity. The company touts that their technology is “broadly compatible with printers, routers, automobiles, telephony, peripherals, point of sale, industrial control, aviation, medical equipment and more.”
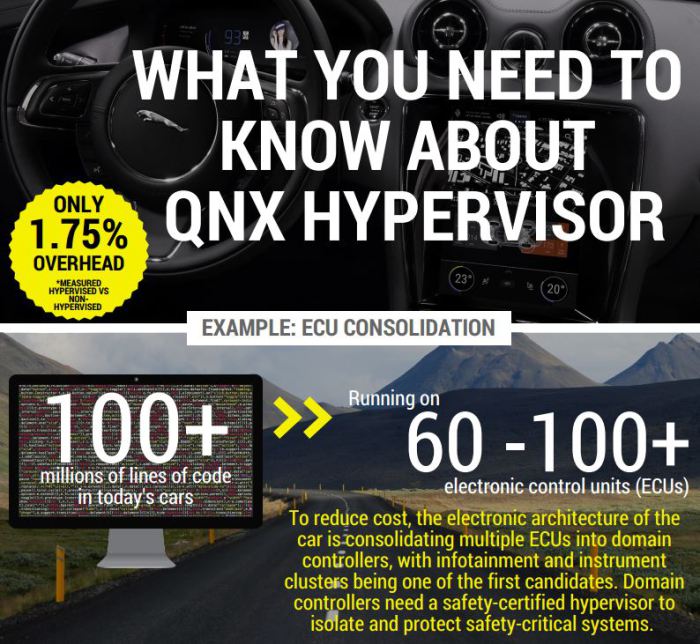
Last month, BlackBerry became the latest entry into the machine cyber security race with the launch of its new QNX® Hypervisor 2.0 software: “BlackBerry’s most advanced and secure 64-bit embedded operating system, enables developers to partition and isolate safety-critical environments from non-safety critical environments, ensuring that no critical systems are put at risk.” The promise of the QNX is to isolate the malware before it impacts critical systems to compromise the integrity of an autonomous machine, specifically a car. John Wall, head of BlackBerry QNX proclaimed, “There is no safety without security. If hackers can access a car through a non-critical ECU system, they can tamper or take over safety-critical areas, such as the steering system, brakes or engine. BlackBerry’s QNX Hypervisor 2.0 safeguards against these types of attacks and is a key component of our multi-level approach to securing connected and autonomous vehicles.”
The market for securing autonomous systems is still in its infancy. While there are thousands of startups and established players in enterprise cyber security, there are still less than 50 in the self-driving and robotic space. Already, we have seen consolidation in this small club with the acquisition of TowerSec by Harman (now Samsung); the purchase of Airilou by NNG, and Magna’s investment in Argus Cyber Security. Any one of the companies mentioned in this article could be next, and quite possibly our lives might depend on it.