“It’s Zombie Time.” – Cipher |The Fate and Furious (2017)
Those are the words during the zombie car chase scene that cyberterrorist Cipher (Charlize Theron) uttered when she hacked hundreds of cars in a New York City car chase where Dominic Torreto (Vin Diesel) had to chase an armored limo to get a suitcase. The plot thickens but if you’re a fan of “The Fast and the Furious” franchise, you’ll know that spectacular car chases are only outdone by the vehicular mayhem that ensues with each passing minute.
Not to be outdone by the previous seven installments, “The Fate of the Furious” not only came at a tremendous cost (the latest installment’s budget is reportedly $250 million) but also shows the evolving potential of a new moving attack surface – connected cars. Connected car exploits are so serious that the FBI recently issued a public service announcement. What is less certain is how cyber insurance would cover such a scenario.
“Life’s simple. You make choices and you don’t look back.” – Han Lue | The Fast and the Furious: Tokyo Drift (2006)
The car chase scene underscores the huge strides that the world is making toward mainstream acceptance of electric vehicles. However, one major technology risk of vehicle automation is cybersecurity. A study by the Institute for Highway Safety (IHS) titled “Emerging Technologies: Autonomous Cars—Not If But When” predicts that partially automated cars will be on roads worldwide before 2025, some fully automated cars will be on the road by 2030, and nearly all vehicles will be self-driving around 2050.
Safety concerns will need to be addressed far in advance of those dates with millions of miles of car data to ensure regulatory bodies are satisfied with the advent of this technology. The nature of mobile, automated hardware (cars) will also need to take into account all the risks that may be posed to the public and how to insure against such physical and virtual damage. Given that human error is responsible for more than 90 percent of all accidents, safety is expected to improve rapidly.
More safety will equate to rapidly falling car insurance but cyber insurance will still be a known unknown. There will soon be a major debate over whether the best way to “protect” these systems is to have a small number of highly guarded and deeply
tested systems or a large variety of systems that are different from each
other (probably built by different companies) and thus not subject to
the same kinds of attacks. The “cloud” predisposes to the first kind of
solution; competitive dynamics in the industry predispose to the second.
According to Mike Weber, VP of Labs at Coalfire Systems, “the traditional fields of insurance, underwriting decisions are made based on data that’s been collected for hundreds of years or more. Cyber insurance, particularly in the automotive field, has maybe 6 years of data.” He believes that the impact of a wide-scale cyber breach will result in radical rate spikes, and there will be vast differences among insurance providers.
“If we have to, overnight parts from Japan.” – Jesse | The Fast and The Furious (2001)
Progress in automotive technology and our desire for improvement also creates risk. A few years ago, the Library of Congress issued exemptions to the Digital Millennium Copyright Act (DMCA) as part of a triennial review. One of these exemptions grants people access to parts of the computer software running their cars for the purpose of “good faith security research” and “lawful modification.” Previously, Section 1201 of the controversial DMCA prevented car owners from unlocking the access controls of their vehicle’s software. With this evolution, automotive technology will give consumers the ability to tinker with the digital hood of a car as much as its physical hood. Similar to “The Fast and the Furious” franchise, it may create a portion of the population that enhances, tweaks, and/or changes onboard automotive systems. Despite controls that may be put into place by automobile manufacturers, the risk of third-party appliances and implementations may result in accidental exposures for vehicles.
“Hey, we do what we do best. We improvise, all right?” – Brian O’Conner | The Fast and the Furious 6 (2013)
The exemptions to the DMCA open the door for the makers of self-driving vehicles to mitigate risk by issuing cyber insurance coverage. Cyber insurance is designed to mitigate losses from a variety of cyber incidents, including data breaches, business interruption, and network damage. Cyber policies typically offer first-party coverage to protect the policyholder against its own expenses after a cyber attack, such as the costs of notifying customers of a data breach, obtaining forensic services to determine the cause of the breach, restoring computer programs and electronic data, or taking measures to restore the company’s reputation.
Dr. Aleksandr Yampolskiy, CEO of SecurityScorecard, can imagine that there will be a future where cars will have associated industry security ratings, similar to the current automotive safety ratings, and one that also lines up with the security ratings also used by other industries. Similarly, insurance companies will be able to incorporate cybersecurity factors into car insurance quotes. For example, if a car manufacturer has a good history of digital security implementations—then that manufacturer’s cars are probably less likely to be hacked.
With the average car having at least 30 million lines of code, the attack surface that cyber insurance must cover only increases with advances in technology and the new threats of such advances. The question that will be posed to insurers is how these new threats will dictate premiums. With the increased sophistication of risks from potential hackers, factors such as driving habits and online cybersecurity postures may become part of issuing insurance policies. To maintain profitability, insurance carriers may require more threat and protection intelligence and develop baseline requirements for issuing cyber insurance policies.
“I live my life a quarter mile at a time.” – Dominic Toretto | The Fast and the Furious (2001)
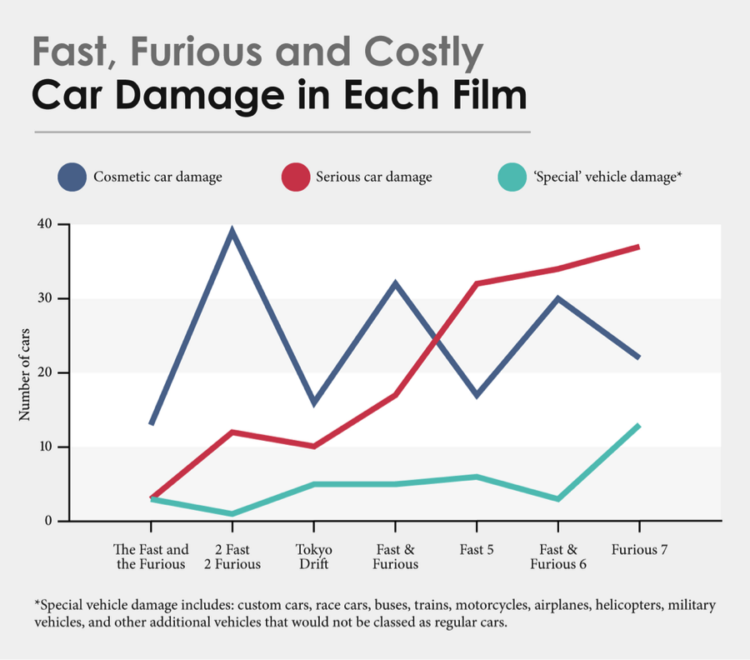
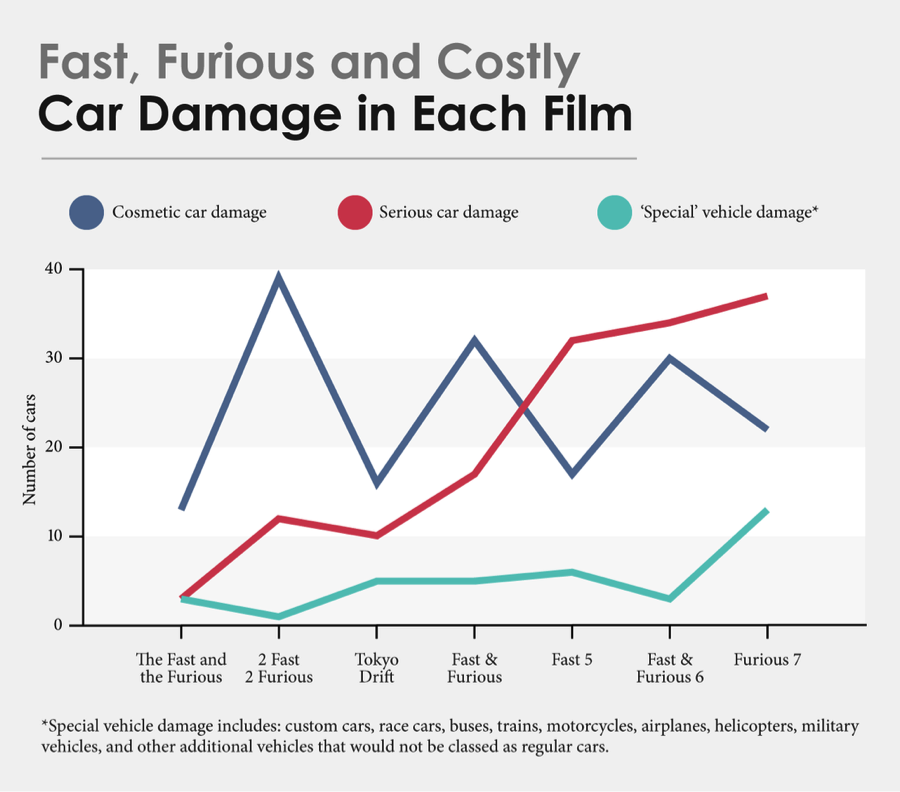
“The Fast and the Furious” franchise has seen increasing levels of destruction with each successive movie. According to InsureTheGap.com, the entire franchise has cost $514 million. Assuming that “The Fast and the Furious” franchise represents the real world, insurers would have probably capped their coverage especially if cars were modified in ways allowed by DMCA exemptions. A policy on such vehicular mayhem would be based on new actuarial calculations and would be issued based on the franchise’s market capitalization, defense and risk profile, attack frequency, as well as the capability to halt attackers such as Cipher and remediate breaches. The increasing sophistication in the way the risks associated with cyber attacks on cars will be factored into policy costs. Also, the attack surface will continually increase as we connect cars more into our lives, phones, and homes. So, while zombie car chases are true black swans, vehicles are increasingly becoming an attractive target for hackers.
“Ride or die, remember?” – Dominic Toretto | The Fast and the Furious 6 (2013)
Given the opportunities that are present in the future of the automotive industry, cyber attacks must be addressed before, during, and after an attack. Cyber insurance is simply a Band-Aid that addresses attacks after the fact. To truly commit to stopping destruction on a theatrical scale, the automotive industry needs to address vehicle safety and security while municipalities need to monitor the evolution of smart transportation. As Steven Weber, faculty director of the Center for Long-Term Cybersecurity at UC Berkeley states, “It’s not just vulnerability to intentional attack, it’s unintentional failures.” It’s going to come down to larger investments from auto manufacturers to support development teams that also include strong security programs and incorporate DevSecOps concepts into their development processes. This includes the automation of security assessments and scans against the software, increased penetration testing for vulnerabilities, and stronger training for developers in secure coding concepts and methods in order to produce more secure code from the outset of a development project.