Although many gaming and entertainment platforms have developed countless versions of VR in the last few years, the use of virtual reality is far from a solely game-driven industry. In fact, the implications of VR in the IT world are enough to provide solid proof that this form of virtual technology can be utilized in the business and tech sectors effectively and continuously alike.
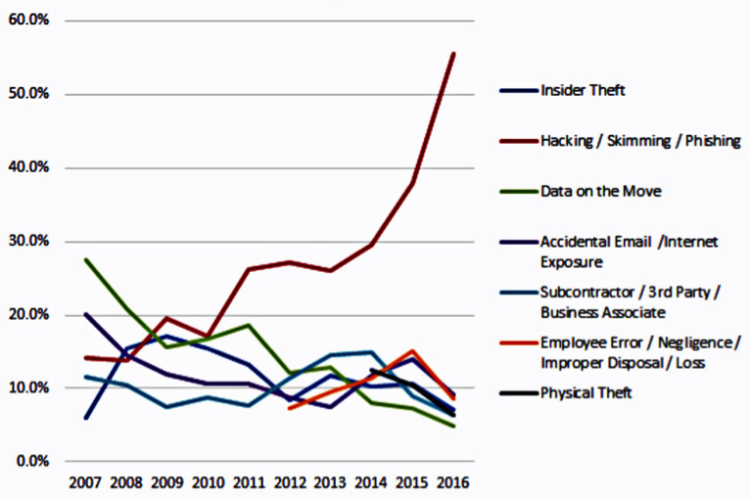
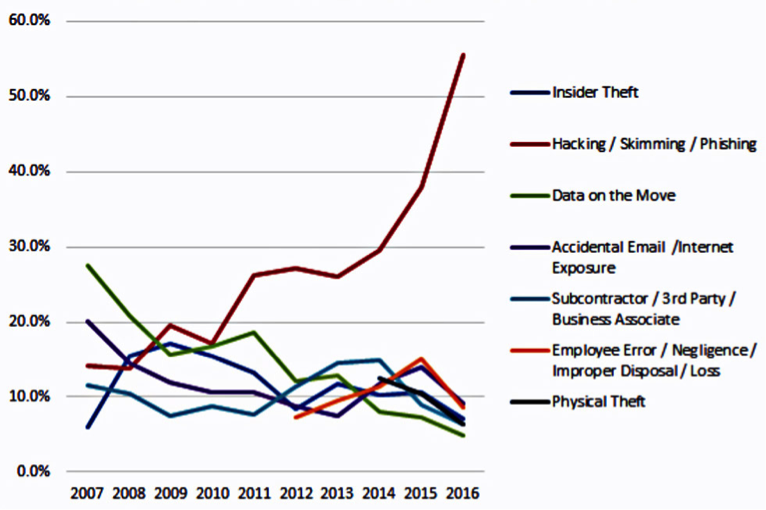
However, despite the immaculate list of pros involved in virtual and augmented reality, the question of cyber and data security still remains. In 2016, the number of reported data breaches increased by 40 percent and 45 percent of all breached organizations were in the business sector. With a device such as a VR headset which is not commonly known to boast strong security systems, modern-day hackers can turn the IoT that these devices are connected to into a platform with which to wreak havoc on businesses, government officials, and even consumers.
However, with every new case of data intrusion, yet another company stands tall and responds with a solution in order to make this form of technology safer in the interim. Furthermore, companies have begun to utilize things such as Steganography and SpatialOS to prevent rather than play offense in this cyber security war and the results are not only positive but also are reforming the way we look at the internet and technology as a whole.
Virtual and Mixed Reality in IT, Design, and Development
In the last few years, since the first virtual reality prototypes were released, companies and consumers alike have been unable to contain their excitement and their demand. In fact, in 2016, 6.3 million VR headsets were shipped across the globe according to a Super Data Report, and over $2 billion was invested in virtual reality according to a Digi-Capital report likewise.
The implications of virtual reality in business have been immense ranging from 3D modeling and testing all the way to 3-DAT data analysis that allows companies to use 3D VR techniques to assess financial and business data. In turn, the future of virtual and augmented reality continues to expand far beyond its original console-based reaches.
For instance, by utilizing CAVE fully immersive virtual reality along with Haptic gloves such as Neurodigital Technologies’ Gloveone showcased at CES and a motion tracker such as HTC’s VIVE tracker, you can not only test and manipulate models, products, and architectural designs but also be able to feel and interact with them as if they were real objects.
Furthermore, the University of Warwick’s Physics researcher, Richard Wellard, created a research company known as 3-DAT to help reduce the time it takes businesses to discover trends and find ways to improve their business model using 3-dimensional data. This kind of 3D technology can be used to track data for IT portfolio management and business model improvements and can help companies in the IT sector review massive amounts of data with ease.
After being part of a team of researchers from Warwick tasked with the difficult analysis of three-dimensional paths of charged particles in near Earth space, Wellard discovered that utilizing 3D technology to analyze the data reduced the time it took to not only compile but rather analyze said data in a far more efficient manner.
Therefore, he created a virtual reality 3D data modeling company dedicated to making data analysis a virtual effort and allowing companies the ability to actually see their data and determine multiple plans for improvement in far more efficient and interactive way. However, even utilizing software such as FileMaker integrated with RESTful API’s, IBM’s Watson Analytics, or Linux’s R or ROOT tools in the future can become wonderful ways to integrate programs currently being used by your business into a virtual platform for better analysis.
Another way companies have begun to utilize Virtual Reality is through its ability to connect various web design tools in order to make web design a far more interactive and easy-to-use process. Although some speculate this could mean a decline in the need for web designers in the next few decades, the market is still rather small and learning to integrate this new tool in your web design department now may help to gain the upper hand if it does become a more substantial form of design in the future. By using VR design tools such as Javascript’s API, WebVR, and looking into some of the ways that Virtual Reality design can be used at Mozilla’s MozVR, you can begin to learn VR design on multiple platforms including the Oculus Rift, HTC Vive, and Google Cardboard.
However, with any connection of devices with low-security standards, the threat of identity theft and data breaches still remains. With 6.3 million VR headsets connected to the IoT, the probability of a massive malware infecting said devices and infiltrating personal data from these headsets is immense and the actions that these VR and IT companies take in the next decade will significantly affect the security of their consumers, companies, and government alike.
Virtual Reality, Augmented Reality, and IoT – Is it Safe?
With the demand for Virtual Reality increasing daily, companies looking to be ahead of their competitors in the release of their VR technology chose to bypass many of the privacy and security standards that would make these devices far more safe to connect to the IoT and various other programs and applications in conjunction with them.
On the subject of supply and demand leading to security issues, Ben Smith, CEO of Laduma, stated, “As new developments are rushed to market in order to gain a lead on competitors, there is a risk that mistakes are being made.” Because of the massive popularity that Virtual and Augmented Reality has gained in the last few years, companies were forced to either put out products that were not necessarily secure or forego their inclusion in the massive VR market of 2016. However, it is no surprise that the connection of multiple insecure devices on a network creates a perfect entry for hackers to retrieve the massive amounts of data which Virtual Reality platforms both receive from the users themselves as well as collect without necessary consent for marketing purposes. In fact, Tata Communication’s Srinivasan CR once stated on the subject, “Every device connecting into a network is a potential vulnerability which can be used to infiltrate the network itself and other devices connected to it.”
When the Oculus Rift was released in March of last year, terms of their agreement stated that they would not only receive basic information from users but also far more personal information such as the user’s email, occupation, date of birth, and place of residence in order to build their marketing analytics and target these individuals based on their location, demographic, and interests. On top of this, Oculus Rift users are also tracked via their online transactions and web and app usage patterns in order for the company to specifically create targeted marketing campaigns that include your personal interests and items you either wanted to buy or need for the items you recently bought.
However, although the company claims to have substantial security measures in place, this collection of data in conjunction with the weak devices connected to the server create a massive opening for identity thieves, data manipulators, visual terrorism, and phishing alike. Furthermore, when using augmented reality such as Pokemon Go or Mixed Reality such as the recent creation from Dan Gottlieb, geolocation is highly important and this poses a threat for many individuals with weak security devices as this makes you traceable and can allow hackers to track your daily routine in order to attack you physically (think back to the people luring Pokemon Go players into alleyways and robbing them) or discovering information such as banks and other location that you frequent which can make stealing your identity even more effective.
Lastly, applications such as OpenSimulator Metaverse’s HyperGrid and Content Delivery Networks (CDN) are another way in which hackers have begun to attack VR users and their personal information. With OpenSimulator Metaverse’s HyperGrid, in particular, you are connected along with various other VR devices via hyperlinks, however, these links are often unsafe which allows for hackers to infiltrate the devices and intrude upon the data collected from them.
Similarly, CDN’s have begun to take hold in the VR world since E3 as they allow for companies to deliver content such as new videos with VR compatibility to their consumers using a system of distributed servers based on geolocation, however, DDoS CDN attacks have continued to rise in the last few years as hackers have discovered new ways to infiltrate the firewalls of these CDN’s and create forwarding-loop attacks likewise time and time again. With this said, utilizing CDN’s in VR could lead to countless infected devices and once again create a botnet which could lead to the leaking and theft of countless consumers’ personal data.
Visual Terrorism, Botnets, Facial Recognition, and Phishing
Although identity theft aspects regarding VR are fairly straightforward in nature, visual terrorism, botnets, facial recognition, and phishing are all slightly more unorthodox ways in which hackers have begun to utilize VR to their benefits. Although many consumers are unaware of these malicious forms of cyber attacks and how they work, they continue to pose a serious threat to VR users and companies across the globe.
Visual terrorism, in particular, is a large concern of multiple countries due to the fact that it consists of intensifying the negative effects that using VR have on a person including dizziness, nausea, muscle twitching, blurred vision, headaches, and seizures. By hacking into weak devices and spreading malware that creates loud flashes, bright colors, or spinning screens, hackers can create mass visual attacks on VR users and even be the cause of some consumer’s deaths in the process.
Furthermore, a team of researchers from the University of North Carolina recently discovered a new way to bypass modern face authentication by using synthetic faces displayed on the screen of a VR device. In the past, facial authentication systems were used in multiple different ways including mobile payment and sensitive data safety precautions for larger companies, however, these past recognition softwares could be easily fooled by the use of a picture in from of the screen. However, now these devices focus on nearly 80 different nodes in a person’s face and textures to analyze their faces in a far more complex manner.
Despite this, the University of North Carolina was able to take a few pictures from each of their tested individuals’ social media accounts and create highly accurate 3D models that were then displayed on the screen of a VR device and put up to the camera of the device looking to achieve facial recognition. In doing so, all five apps that were tested were unaware of the difference between the real thing and the 3D model posing yet another unconventional yet highly terrifying security threat for companies and consumers alike.
Similarly, phishing is another way that hackers can utilize this tech for their malicious intent. Phishing is a technique in which hackers create false identities in order to trick individuals into doing things they would not normally do. For instance, by hacking into VR headsets and using fake virtual objects or pretending to be updates for the system, consumers may unwittingly deploy trojans into the network or leak their passwords to hackers leading to a far easier entry way for hackers to manipulate data in the cloud.
Another threat which has been seen quite often in the last year within the IoT, in particular, are botnets spreading malicious malware such as Mirai into connected devices leading to massive DDoS attacks. Mirai malware, in particular uses a table of nearly 60 common factory default usernames and passwords to target devices with weak security and infect them with the malware. From there, these devices monitor a command and control server to to bypass anti-DoS software.
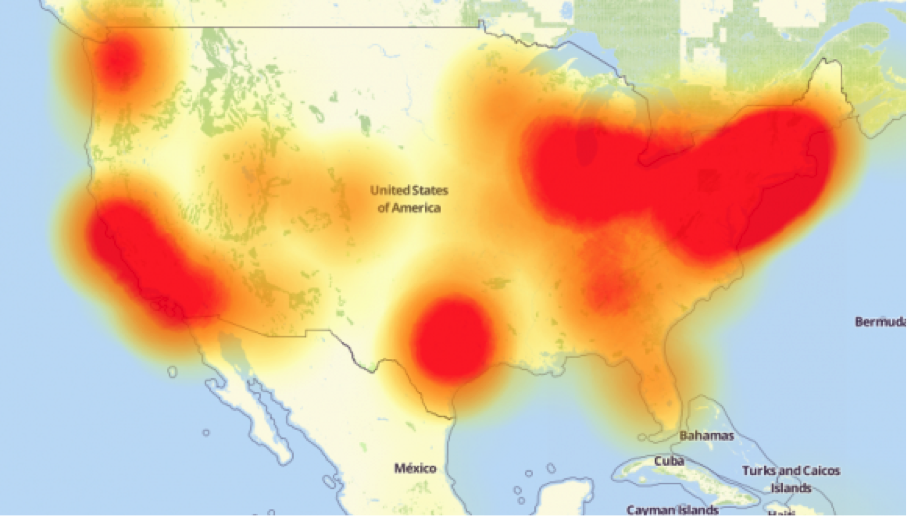
Along with BASHLITE, Mirai Malware infected a myriad of weak cameras connected to Krebs on Security in September of last year and had the largest attack strength in history at 665 Gbps, however, this was far from the most powerful attack on the IoT performed by this malware. In October, only one month after the attack on Krebs on Security, Mirai Malware infected countless more devices and previously infected cameras from the Krebs attack combined with these newly infected devices and joined a network which included multiple high-profile companies on a DNS service provider known as Dyn. This led to the inaccessibility of multiple large websites including Github, Twitter, Spotify, Reddit, Netflix, and more.
This attack set a new record that was staggering at best clocking in with an attack strength of 1.2 Tbps. In response, ARM CEO, Simon Segars, stated, “If you’re a device maker building IoT products, you really ought to be worrying about updating the firmware that’s in it.” In fact, ARM has since then developed Mbed Cloud to help companies push updates to their device’s chips and customize OS in order to prevent malware attacks such as the DDoS attacks on Dyn and Krebs.
On top of this, multiple other companies have begun to take botnet security extremely seriously implementing new devices and programs to prevent data intrusion and DDoS attacks alike. Securifi, launched January 23rd of this year, in particular, has decided to help the IT professionals looking to utilize VR or retrieve data for their company at home by creating a device which specifically defends against botnets to ensure that your home devices with weak security are not affected by hackers in the long run.
What We Learned From Mirai Malware
One key thing that IT professionals as well as both Dyn and Krebs on Security were able to determine by analyzing the attacks was that they primarily came from cameras and DVR’s with weak security. The issue with this is the fact that it showed us that weak security home devices, in particular, are what Mirai tends to target. With this being said, the push for VR without following proper security measures as well as its dependence on the average consumer whom typically does not focus on security and utilizes weak passwords or default settings all too often may be the perfect formula for malware such as Mirai to create its third record-setting DDoS attack.
In fact, multiple companies claim that this attack proves that AI’s utilized in weak security devices like VR headsets and cell phones will undoubtedly be the next systems attacked by malware and hackers in 2017. Although companies like T-Mobile, Oculus and Sony have promised higher security standards in the next few years for their devices and T-Mobile is taking measures regarding their 4G LTE network to ensure Cloud Security, the issue is still more than prevalent today and its effects could spell serious data breach damage.
On the subject, Alex Matthews of Positive Technology even said, “AI agents will be, perhaps, the most dangerous VR objects. AI is a hard task for security checks since the range of its actions and reactions could be pretty wide.” With this said, it is no stretch to assume that 2017 will be the year of VR data breaches and the companies combatting it will continue to help businesses utilize VR without the fear of becoming a victim of data intrusion in the process leading to a continuation in the expansion of VR technology and its profitability alike.
Similarly, after Krebs on Security was attacked, Brian Krebs stated, “The internet will soon be flooded with attacks.” Despite this seeming rather dark in nature, Krebs and the countless other IT professionals witnessing the effects of connecting weak devices to the IoT may not be far off. By analyzing data from attacks such as these two and learning how to counteract them, we can ensure that the millions of VR users out there including the countless professional settings which utilize this new tech for data analysis specifically are not the next target for the malicious world of hackers and their botnets alike.
Using SpatialOS, Steganography, Cloud Security, Botnet and IoT security, and Load Balancing to Promote Data Security
As data security has become an issue in VR through the IoT and multiple companies have seen the incredible impact VR can have on data analysis, 3D modeling, and more, therein lies a disparity between security and insecure devices, which multiple companies are choosing to tackle head-on. For instance, when two representatives from the British government came to the company Improbable in order to use their SpatialOS to create a 3D model of the internet, Improbable rose to the occasion with style.
By using SpatialOS, they were able to demonstrate a dynamic model of Border Gateway Protocol (BGP) at scale and study it for various weak spots in order to determine where hackers could attack or were attacking currently. In doing this, they were able to prevent multiple data breaches before they ever became a problem and the use of this form of 3D modeling continues to be an impressive but extremely useful tool for governments to regulate weak devices and the companies providing them.
Furthermore, with companies hopping on the VR bandwagon left and right, accessing data remotely to work from home on virtual models or the testing of products using 3D technology is slowly becoming yet another way for hackers to attack the weak VR devices and access sensitive information from companies world wide. Therefore, the use of steganography in files which can be shared to the VR such as audio or video is slowly becoming a more common process.
With so many of these VR devices connecting to the cloud to become a part of the IoT, companies have tried to target the weak points in cloud security in order to protect these connected devices. However, because of the sheer amount of data being provided, some individuals speculate that using PCI DSS security standards and data anonymization techniques are our only hope at combatting data insecurity.
For instance, with PCI DSS data security standards, they tend to focus on ways to build cloud security as well as CDN security and increase concurrent users and the reliability of apps by load balancing likewise. Furthermore, Teesside University’s Joao Ferreira is a huge proprietor of data anonymization and has even said in the past, “New data anonymization techniques will be required so that the new data being collected by VR devices does not identify its originator.”
Lastly, IoT security measures to prevent botnets have slowly risen in the tech world. In turn, devices such as F-Secure and Norton’s Geodesic Dome have been developed. These devices prevent your weak home and office tech from being hacked into and also support IoT and cloud security likewise. By using these devices in office VR endeavors, companies can ensure their VR headsets are safe no matter how insufficient the actual technology may be and reap the benefits of virtual reality in business without the unfortunate consequences all too often associated with it in return.
In the end, it is not surprising that these incredible virtual and augmented reality headsets are becoming the bricks with which the future of technology in business is paved. However, by knowing where to step on this road and ensuring you remain safe in the process, you can continue on into the future without falling victim to the crippling effects a data breach can have on your business. With this said, the future is now, virtual reality is finally a reality, and the impact on the internet, security, and our lives that it will have continues to expand each and every day.