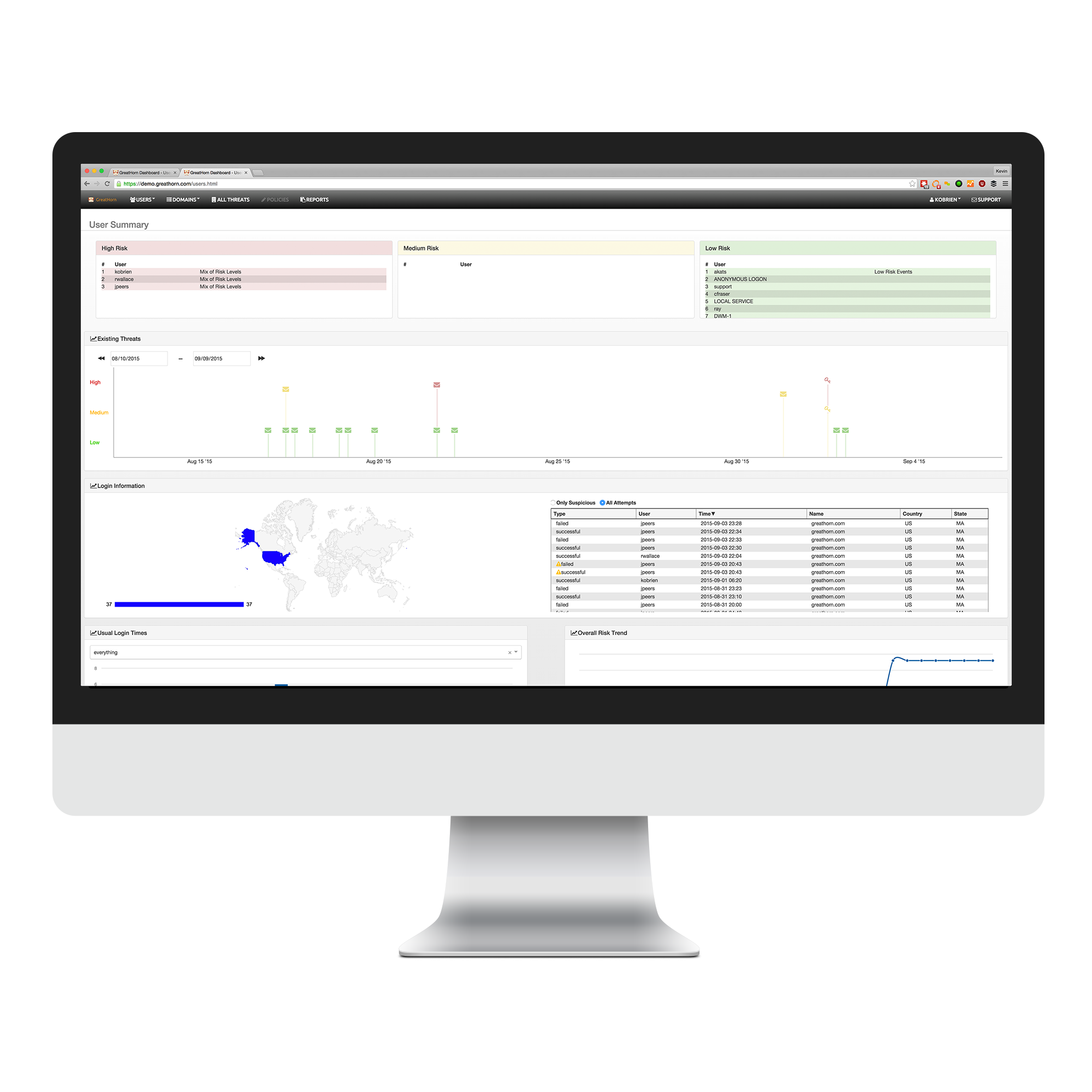
The amount of personal and business information that lives in the Cloud is overwhelming. The endless space is so attractive and it is clearly the future of storage, but in the back of your mind you a re a little weary that hackers can access your information at will. Well, if you believe you are better safe than sorry, then GreatHorn is for you. Pooling their years of experience GreatHorn can help your company stay safe from breaches and specialize in Email security.
CEO Kevin O’Brien, explains GreatHorn’s vision, and how their expertise of spear phishing is making companies safer.
Tell us about the decision to apply for the Techstars NYC?
I’ve had the privilege of being an early and in some cases founding member of a number of technology startups prior to GreatHorn, and have had the chance to see and help test a number of forms of early growth strategies over the last 15 or so years.
While evolutions in technology have made it much easier to stand up a new venture than ever before – very few entrepreneurs today grapple with phone systems, server racks, or multi-month deployments for on-premise CRM systems, for example – the bar has also risen for demonstrating real traction. As more and more startups compete for visibility, customers, and product market fit, it’s increasingly important to “prove it” before taking in capital and hitting the gas on the business.
Techstars helps do just that. Both from the perspective of offering a base of good startup fundamentals as well as highly targeted strategic insight into each team’s business, their model and broad network of companies, mentors, and fellow entrepreneurs offers something that no other early stage accelerator can in terms of getting critical early validation. For us, even as a team of “veteran” startup founders, Alex and the team at Techstars NYC was an incredible opportunity to do more faster.

Tell us about your product or service.
GreatHorn is a cloud based cybersecurity platform that prevents the kinds of cyberattacks that have dominated the news this year, from Anthem to Ashley Madison to OPM.
Let me start with a story. We have an early customer who runs a health insurance company in Boston; they’re a key part of the MA healthcare space, offering insurance through our state connector website, and help small businesses throughout the Commonwealth meet their state and federal insurance requirements.
They run as a startup; their tools are all in the cloud, they’re incredibly focused on providing amazing service, and they have a great understanding of security and compliance but finite personnel and resources to dedicate to the problem.
In the wake of the Anthem data breach, the Board of Directors for this startup asked their CIO how they were going to not be the next big breach. For them, the damage from that kind of an attack – both financial and reputational – could be fatal.
We spent time in their office, walking through both how these kinds of breaches happen and also understanding where their needs were. As an early stage team, we’re sympathetic to the resource allocation challenge, especially for security. We’ve gotten really good as an industry at preventing malware, software exploits, and other forms of technological threats, but we’re still woefully underprepared when it comes to detecting and preventing highly targeted trust-based attacks. It’s why over 90% of all big breaches start the same way: criminals research a company, register a new domain, and use it to impersonate someone via email that their target trusts; from there, they get illicit access to either credentials or finances (often wire transfers), and wreak havoc.
For a company like this one, having trainers to come tell your staff to not click on links represents an outdated approach to an ever-more-sophisticated problem. Instead, we were able to help them solve it by automatically analyzing every inbound email, looking for and providing defense against their entire landscape of electronic communication. They were able to take those results to their Board, and demonstrate that from both a regulatory and operational perspective, they were 100% on top of these kinds of threats.
What is spear phishing?
Everyone knows what phishing is: spray-and-pray style emails that try to trick you into clicking on a fake PayPal or eBay link, sent to hundreds of thousands addresses, with very little thought. They’re often rife with spelling and grammatical mistakes, and are easy to spot.
Spear phishing is phishing’s big brother. It’s the same idea – a fake website or identity is created to trick someone into doing something for the benefit of the attack, such as authorizing a wire transfer “from the CEO”. What’s different about it is that it is multiple orders of magnitude more sophisticated, and has a track record of success in helping nefarious groups break into or steal from even very large, very smart companies.
How is it different?
The big difference is in how clever spear phishing attacks can be. To give a simple example of that, we look at nearly a dozen different factors for every email we analyze, all separate from the content of those messages, just to baseline what is or is not a spear phishing attack.
What market are you attacking and how big is it?
Our plan is to be the world’s leading email security provider; every information security and technology professional is being asked how to prevent these kinds of attacks, and we’re uniquely positioned to detect and prevent them. (We’ve tripled our customer base since coming to Techstars, and the market here is huge.)
GreatHorn fits into the broader landscape of the cybersecurity market, comprising a wide range of both software and services companies which consume annual CIO/CISO budget. In total, this market is currently estimated at $71b, and is expected to reach $155.74b by 2019 (per Forrester’s 2014 Market Overview report).
What is the business model?
We’re a SaaS-based security company, and we’re integrated directly into the world’s most popular email systems: Google Apps and Microsoft’s Office 365/Exchange offering.
When a company signs up, we can typically deploy to them in under 20 minutes, and provide realtime analytics and defensive capabilities within a couple of hours, offering complete coverage for every user in their organization.
Why did you embark upon this venture?
Having spent over a decade and a half in security (each!), the founding team at GreatHorn strongly believes that the intersection between “hard” and “important” problems are where the most critical work in security will be done. Failure to protect against data breaches results devastating losses of highly personal information, it fuels criminal activity on an international scale, and it’s responsible for financial damage that leads to economic harm on both an organizational and personal level for companies of all sizes.
It’s why we say “security is a basic right”, and we live it every day.
What are the milestones that you plan to achieve within 6 months?
Our focus is 100% on growing a massive security company; we’ll be focused on continuing our rapid customer growth while at Techstars, and making strategic investments across both team and product to align for long term success.
What are you looking forward to doing the most in NYC outside of work?
We’re all serious foodies, and have been incredibly excited to sample all kinds of restaurants, markets, and awesome meals while here. (We’re also super excited by the fact that two fantastic meal-based companies are part of the current Techstars batch!)